4.3.2.3 Static TLS certificates
Last updated
Last updated
Traefik requires access to the content from 2 certificate files which your certificate supplier must provide to you. In the previous step these were created by certbot for LetsEncrypt but other certificate providers will provide equivalent files albeit they may be named differently. The files that Traefik requires are:
.crt
This is the certificate "Full Chain File", equivalent to the fullchain.pem file that is created by certbot. The full chain file combines both your domain's certificate and the intermediate certificates in a single file.
.key
This file holds the private key associated with your SSL certificate, equivalent to the privkey.pem file that is created by certbot. It's crucial to keep this file secure and private, as anyone with access to it can impersonate your domain.
Static TLS certificate files have an expiry, therefore they need to be refreshed. The default country configuration doesnt provide an automated way to do this, but the following snippets explain how static files and their refresh can be automatically configurable going forward.
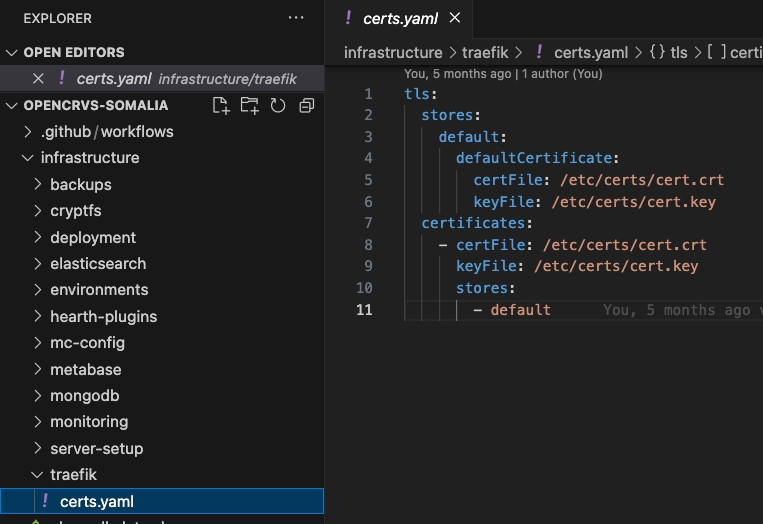
In your countryconfig repository code, create a folder named "traefik" in the "infrastructure" folder and create this certs.yaml file inside of it:
Content of certs.yaml:
Edit the docker compose deploy files to ensure that the Traefik service can access the .crt & .key files that the provisioning Ansible script will create from Github Secrets and the cert.yaml file.
You will have to edit the "Provision" Github Actions to write the contents of the .crt & .key files in the /data/traefik/certs directory on your server from new Github environment secrets you will manually have to create. In the file infrastructure/server-setup/tasks/traefik.yml, add these lines at the end of the file:
Add these 2 new Github environment secrets SSL_CRT & SSL_KEY to the "Set variables for ansible in production environments" step in the file .github/workflows/provision.yml
After you have created Github environments by following the steps in 4.3.4 Create a Github environment you will be required to manually create the following Github environment secrets to store the contents of the certificate files.
The content of the .crt file, ie: the certificate "Full Chain File", equivalent to the fullchain.pem file that is created by certbot
The content of the .key file, ie: the private key associated with your SSL certificate, equivalent to the privkey.pem file that is created by certbot.
When you run the provision action, the files will be created on your servers appropriately.
When it is time to refresh your certificate files, you will need to do the following steps:
Replace the content of the Github environment secrets SSL_CRT and SSL_KEY with your new certificate content.
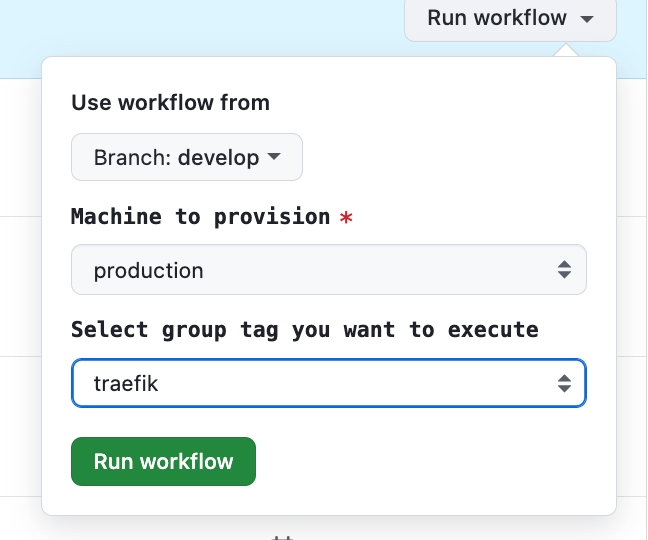
Run the provision action on your servers again. To save time you do not need to run all the provision tasks. You can select simply the "traefik" task and run that.
Re-deploy OpenCRVS. Re-deploying OpenCRVS is required so that the traefik service is refreshed to load the new content from the .crt and .key files.
If re-deploying OpenCRVS did not refresh the certs, you may need to restart the Traefik service manually. Re-starting Traefik is sometimes required so that the Docker container volume for the traefik service is refreshed to load the new content from the .crt and .key files.
SSH into the server and run this command to take Traefik down
Run this command to start Traefik again